
Zero Trust Strategy for Holistic CyberSecurity
In today's world where everything is everywhere, a Zero Trust Strategy represents a paradigm shift from higher walls to intelligent gateways. Our approach converges business and security goals, focusing on business continuity and a resilient growth foundation for business leaders. Beyond traditional models, Zero Trust hinges on three principles: stringent and continues access validation, minimal required privilege, and perpetual breach vigilance. Zero Trust isn't just a security strategy; it's a mindset realignment. By aligning security with business objectives, it strategically shields strong controls where needed and minimises sensitivity where needed. Join us in redefining security as a business enable, propelling businesses forward with confidence.

Why Zero Trust
As the digital landscape continues to evolve and the threat of cyber attacks becomes more prevalent, Zero Trust emerges as a game-changing approach by prioritising assets and providing a robust and all-encompassing security solution.
Here are some of the key reasons why organisations are implementing Zero Trust:
- Agile and Productive Business
- Operational Efficiency and Cost Reduction
- Empowering Regulatory Compliance
- Enhanced IT and OT Scalability
- Asset-Centric Security
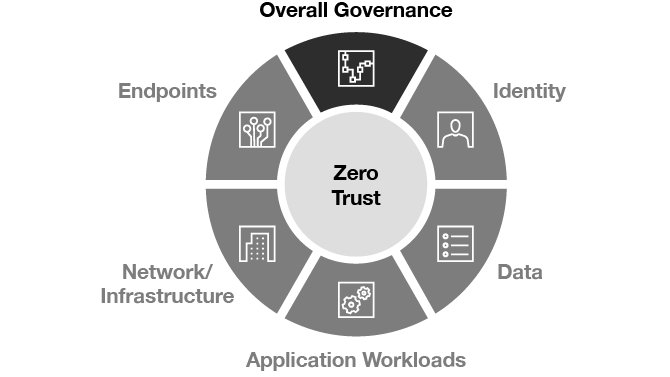
PwC’s Zero Trust Framework
Our Zero Trust Framework is a comprehensive strategy that harmoniously integrates business goals with security measures, laying a strong foundation that fosters secure growth.
- PwC’s Zero Trust Framework
- Identity
- Data
- Application Workload
- Network/Infrastructure
- Endpoints
- Overall Governance
PwC’s Zero Trust Framework
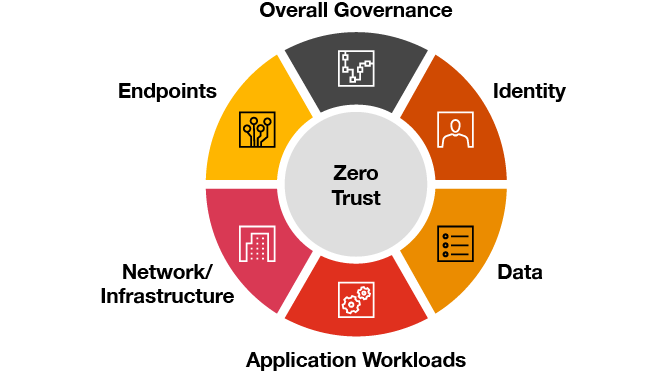
This framework takes a big-picture view of security while seamlessly orchestrating all of these pillars and automating decision making where possible.
Identity

Verify and secure every identity with continuous authentication across your entire digital estate. This includes human & non-human identities.
Data
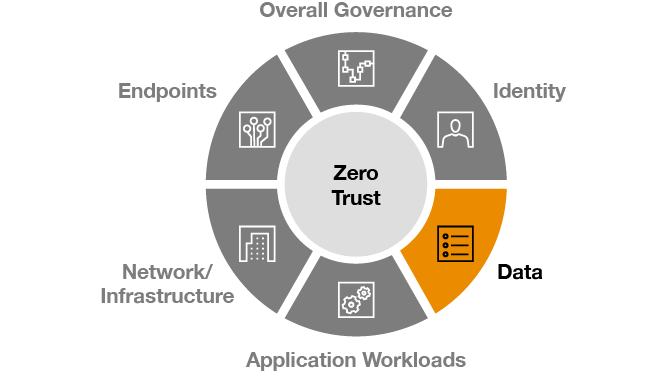
Classify, label, and protect data with end-to-end encryption.
Application Workload
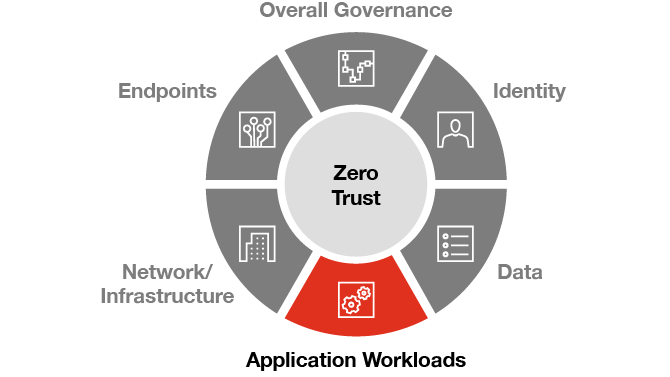
Discover Shadow IT and control access with real-time analytics and monitoring, but also includes application development life cycle and change management
Network/Infrastructure
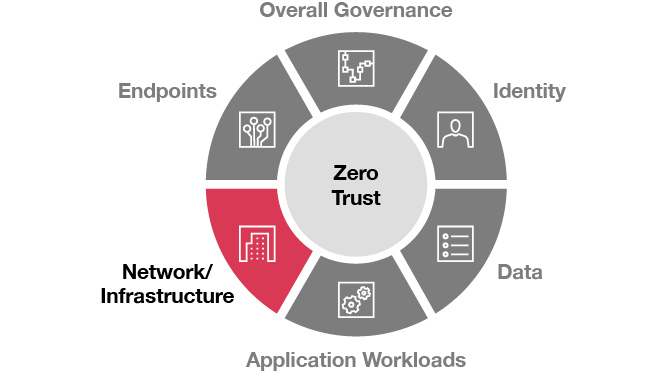
Encrypt all internal communications, limit access by policy, and employ microsegmentation and real-time threat detection. This also includes cloud security, physical security, & network security.
Endpoints

Gain visibility into devices accessing the network and ensure compliance and health status before granting access. This also includes mobile devices, workstations & servers
Overall Governance
This includes security awareness campaigns, performance management & monitoring
How can we help?
As we step into a new era of security, PwC is here to support your organisation's in increasing Zero Trust maturity. Our comprehensive range of services is crafted to fortify your organisation's security posture.
Our approaches to Zero Trust
- Zero Trust Assess and Design: Navigating a Secure Future
Our experts collaborate to understand your unique risks, design a security blueprint aligned with your goals, and assess your current setup to identify enhancements. With a focus on Zero Trust principles, we offer a clear roadmap towards a secure future, ensuring business continuity while enabling your organisation to grow.
- Zero Trust Readiness Assessment: Charting Your Path to Zero Trust Maturity
PwC’s Zero Trust Readiness Assessment evaluates your organisation’s readiness for Zero Trust principles. With vulnerabilities identified and actionable recommendations reported, our Implement and Operate service ensures a seamless transition from design to operational implementation, adapting to emerging threats.
Do you want to learn more about Zero Trust?
Contact us

Partner Cybersecurity, Privacy & Resilience, PwC Netherlands
Tel: +31 (0)63 086 15 22



















